CloudFlare & The Urgency of Cloud Security
CloudFlare & The Urgency of Cloud Security
Abstract
It is safe to believe that the pandemic was a blessing in disguise for the cloud adoption markets. Businesses had no choice but deploy remote working and monitoring infrastructure as far as possible so that the dependency on manual processes is minimal.
To give a quick run-through, the cloud spending grew by 37% in the first quarter of 2020. Capitalizing upon this urgency to drive the processes remotely and securely, cloud service providers had an unlikely successful year.
“Pandemic will harness growth and will drive enterprises towards full adoption to a wider cloud regime which would help the industry breach the $ 1 trillion mark by 2024.”
IDC Report
Both, Public and Dedicated “cloud as a service” models are expected to witness immense growth in terms of revenues during the above period. IDC further predicts the majority of the contribution to
this growth to come from “as a service” products.
It also states that due to the availability of a bigger market, the industry will enjoy a growth rate of 8.3% CAGR. IDC identified increased usage of automation in cloud migration as a reason for this
comparatively slow rate of growth.
The below analysis from Grand View Research is a testimony to the fast paced adoption of cloud products and services across different sectors in the U.S.
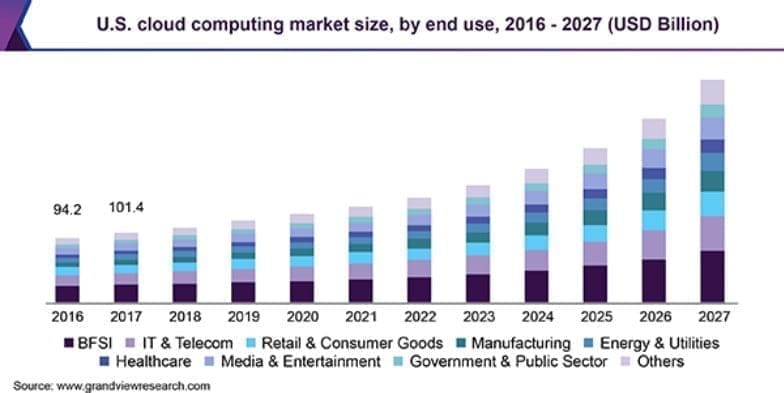
In the following whitepaper, we walk you through the key drivers towards cloud security solutions and the role of CloudFlare.
The Rise of Cloud
Rise of Platform as a Service (PaaS)
Platform-as-a-Service (PaaS) provides infrastructure to develop and store applications in the cloud thereby eliminating the hassle to execute the same on in-house resources. This makes it easier for businesses to drive a range of services such as strategic storing of data (database management), endto-end development and testing of apps, operating systems and running network security protocols.

Over the years, SMEs have extracted the on demand tools to build innovative products at lower costs. This is exactly how underfunded start-ups run by micro teams have been building enterprise grade products and resolved critical issues around.
Edge Computing
Mainstay In The Design To Security Approach
As more devices are connected with each other using the internet, most of them are at the risk of getting attacked for data theft. Chief Security Officers (CSO) are adopting DevSecOps using the “Design for Security” approach and Edge is becoming a primary choice for them to enable secure cloud-based solutions.

What is CloudFlare?
Cloudflare is a cyber security product that provides protection against threats such as identity theft, DDoS theft and SQL injection. It is a free CDN (Content Delivery Network) and delivers optimal site performance while speeding up loading times. It does so by using multiple data centers all over the world including China. It is not incorrect to say that the Cloudflare operates like a giant VPN. For an example, the site visitor would be redirected to the closest possible physical server. Closer the data center, lesser the access time and thus faster the website loading.
The product is largely popular among small to medium scale enterprises those who are looking for supercharging and securing their digital assets.
It offers sophisticated CDN, security, and privacy services-based solutions for enterprises, developers, teams, and individual consumers.
Acting as a reverse proxy, Cloudflare is the wall that requests have to go through to reach your site.
How Does Cloudflare works?
Cloudflare works on 3 verticals of Security, Performance, and Reliability offering the best to both you and your visitors. Cloudflare shores up security, by scanning the requests that are targeted at your web application, looking for malicious content based on suspect IP addresses, the kind of resources requested, the request payload and its frequency, and a firewall that includes rules defined
by you, the customer.
On the Performance vertical, Cloudflare uses several techniques to deliver smooth content to your visitors, by caching static content on Cloudflare data centers and forwarding requests to origin sites in case of dynamic content. Cloudflare also uses intelligent routing over its 200 strong data centers, strategically located across the globe.
On the Reliability front, ClouFlare turns out to be one of the most reliable in the industry with 738 billion DNS queries resolved per day across 25 million internet properties., that include major e-com sites, govt agencies, and enterprises.
Technically Cloudflare acts as a reverse proxy, which means all traffic will be routed via Cloudflare servers which are spread over 200 cities worldwide. The figure given below will shed more light on how Cloudflare is set up to secure and enhance your web assets.
What makes Cloudflare different?
Cloudflare’s architecture gives you an integrated set of L3-L7 network services, all accessible from asingle dashboard. It is designed to run every service on every server in every data center across our global network. It also gives your developers a flexible, Internet-scale platform to deploy serverless code instantly across the globe. No software or hardware is required.
A global immune system for your network
We have built security into every component of the network. Cloudflare’s 100 Tbps network blocks an average of 70 billion threats per day, including some of the largest DDoS attacks ever recorded. Each and every login, request, and response that goes through our network strengthens the machine learning that we apply to detect and block threats at the edge, before they ever reach your organization.
Compliance and privacy are built-in
Cloudflare’s network is built with data protection in mind. We are a privacy-first company with endto-end encryption. We comply with local regulations for data locality and storage. We do notgenerate revenue from advertising, and thus default against the collection and retention of personal data we process on your behalf.
What Data Does Cloudflare Collect From The Edge?
Ever wondered what the Cloudflare Business is all about?
Well for starters it has never been built around selling ads or tracking customers. It rather focuses on minimizing the collection of personal user data. The metadata collection process by Cloudflare is quite technical and tedious.
Cloudflare largely collects extremely limited personal data from our global edge network and sends it to our Core Data Center in the United States for further processing. This data is very simple and can be usually found in the form of IP addresses.
One this data is pooled in together, it is sorted out in to three main categories namely:
- System Metrics and Debugging
- HTTP Request Metadata (used to operate the network)
- Collection for Cloudflare Data Analysis Products
What Are The Benefits for Collecting Data With Cloudflare?
Although there are several benefits of using Cloudflare for website owners in the present day scenario, here are a few things you cannot miss to learn about:
First and foremost, Cloudflare allows you to protect your internet presence. Security has and will always be a big factor for people when using the internet. It is irrelevant if they are business owners or potential buyers online.
Not only this, you can also secure and accelerate other things like websites, apps and even APIs in just a few minutes by providing us with your DNS.
The process of setting up a domain with Cloudflare is pretty simple and can be finished in less than 10 minutes. You also get to keep your hosting provider with you without having to make any code changes.
You also get help with boosting your website/app/API’s performance with our services that include CDN, DNS, DDoS protection, WAF, Web Analytics, bot management, image optimization, SSL, loading balance and stream delivery.
Get unmatched protection for all your products with Cloudflare’s global CDN, unmetered DDoS protection and more.Cloudflare also accelerates and protects any external, public-facing web properties as well.
Website developers often have a precise idea of what Cloudflare can do for you but the same can’t be said about the others. There are a lot of things that Cloudflare can enable you to do. Let’s dive in deeper below:
Build Serverless Applications With Ease
You can use Cloudflare workers to deploy serverless code in a jiffy across the entire web. This gives your website or app exceptional performance and also makes it more reliable and scalable.
Enjoy Our Serverless Platform For Making New Apps
You can either make a new application from scratch or augment any existing app without having to deploy an infrastructure. Our serverless platform makes everything seamless as it uses an isolate model instead of conventional models. Because of this you don’t have to manage scaling, select regions or shed coins for capacity that you don’t use on Cloudflare.
And so you can say goodbye to cold start times with your app. Once the code is live and running across every data center in our network, you are virtually milliseconds away from every internet user.
Implement Zero Trust Access
Use Cloudflare for teams to protect your workforce around the world. The best thing is you don’t need any software, hardware or complicated licensing procedures to get started with this.
Protect Internal Operations on Our Single Worldwide Network
You can use our device-friendly agent or app to turn on Zero Trust Services. Connect directly with Cloudflare’s network for ingress/egress to all your offices, internet and cloud providers. This is the easiest and the best way to protect your employees, office network and also any data centers.
Code Minification
This smart feature allows you to remove any unwanted characters. These include comments, block delimiters, white spaces, newline characters. These characters are not needed to serve a web page. This eventually reduces the file size and helps the page to load faster.
With Cloudflare you can now support these three different types of minification:
- CSS
- Javascript
- HTML
Extra Protection With Cloud WAF
Cloudflare WAP [ web application firewall] keeps CMS and OWASP vulnerabilities without slowing down the speed of your website. We have more than 150 rules that protect your app/website from any kind of web attacks. It only adds less than a 1 millisecond latency to your app.
By using Cloudflare WAF available in our PRO plan you don’t need to update rules for new web vulnerabilities as our cloud based security specialists are here to do just that.
Get A Free SSL
Having a SSL is extremely detrimental for any app or website these days. A SSL allows your app to get access over HTTPS and makes sure that all data is encrypted from your user’s devices to your server.
What’s more is a SSL is now also considered as an important factor for ranking on search engines. We provide you with a SSL certificate free of cost and also give you the provision to upload a certificate if you already have it.
Make The Most Out of HTTP/2 Protocol
Did you know that Cloudflare uses the new HTTP/2 protocol which is 2x faster than it’s predecessor HTTP/1. This gives you the edge to load several page elements at the same time over a single TCP connection. It also helps you with push technology and compressing the header.
With Cloudflare you use HTTP/2 acceleration by default without any required configuration. We are now also proud to offer our customers with HTTP/3 support.
Load Balancing
The Cloudflare Load Balancer works smartly by distributing all your web traffic to several servers. This feat ensures that your website/app is always up, available and running in case any backend server goes down. This decreases load time and gives better access to your users.
The Cloudflare load balancer also supports health checks, geographic routing and automatic failover for your app.
AMP Real URL
This advanced feature utilizes the HTTPS for authenticating the given content when served from the AMP cache of Google. As and when the Cloudflare AMP real URL detects any supported browser, it starts creating signed exchanges for the content requested.
There are several benefits of using AMP pages; it helps boost loading speed on mobiles by optimizing pages for asynchronous script loading that have a quick rendering time. AMP pages also perform higher on SERPs which is why they are good for doing mobile SEO.
Cloud Security in 2022 & beyond – Better, Bigger and Accessible to all
It takes a simple cyber-attack to ruin the reputation of your business built over the decades. Yet most enterprises didn’t wake up until the COVID restricted their workforce to operate from unsecured home offices and prone to attacks such as phishing, identity theft and hacking. Those who had implemented necessary security protocols in advance sailed through while others had to face the wrath. Millions of home systems were left exposed to threat agents that grew by 630% in the first two months of the lockdown. As a result, enterprise consumption of cloud services
immediately grew by 50% to accommodate critical workloads.
In 2021, cybersecurity is even more imperative because most corporates would want to continue with extended WFH. More WFH, more exposure, and more attacks will further increase the demand for cybersecurity verticals. For millions of small scale companies that can’t afford an overnight revamp of their technology facet, the cloud is transpiring as the most effective solution to delegate, operate and monitor remotely. Needless to say, more cloud means more emphasis on cybersecurity.
As per these recent findings from ABI Research, the cybersecurity spending for Critical Infrastructure (CI) could value USD 105.99 billion in 2021. Therefore, the emphasis to on demand access to data and processes cloud will need the backing of innovative solutions like the Secure Access Service Edge (SASE). For faster and safer adoption of the cloud, here’s what enterprises should do with their cybersecurity strategies in 2021.
Include more Automation
Automation in security has always been a preferred subject for many researchers and now is the time to put it to execution. In its simplest use case, AI-enabled communication bots can cover up for understaffed departments. Moreover, since automation reduces human dependency, detecting and investigating threats and resolution to low-risk threats can be left to Machine Learning (ML) based algorithms. ML can programmatically notify potential attacks or other loopholes in the system.
In the post-COVID era, this will be a great support for enterprises that want to continue with a minimum workforce. In fact, they can maximize their resource utilization towards other tasks. Cybersecurity is a huge domain and restricts the teams from 74% of other organizational events or key seminars.
Time for SOC-as-a-Service
Security Operation Centers (SOC) display enterprise systems and their interdependency across departments and verticals on a centralized dashboard. With such in-the-moment monitoring and analysis of processes, able to respond proactively and circumvent cyber-attacks. Moreover, such a bird’s eye view enables the decision-makers to identify key areas of investment and thus utilize
resources more efficiently.
Although SOCs were always an essential pillar of the corporates, the cloud is making them a reality for SMEs. With subscription-based models, cloud managed services providers are offering less expensive maintenance of security processes. Besides an opportunity for SMEs to have their own SOC, clouds ensure security implementation for the smallest of business models. Moreover, they seek direct access to expert teams of expert teams of engineers and security analysts.
As a part of the cyber-security-as-as-service, SOCs work closely in line with security information and event management (SIEM) processes.
Given the increasing workloads and paradigm shift to the cloud, SOCs are expected to grow at a CAGR of 28.6% (2020-25) and will form an important pillar in digital transformation initiatives.
Extended Detection and Response
Packaged solutions are a key offering of the managed services in the cloud. For cybersecurity, enterprises can benefit from SaaS-based incident response and threat detection tools. Labeled as Extended Detection and Response (XDR), the service wraps all essential security products into a unified operation. The teams here work with the SOCs and seek a holistic view of the operations across the organization.
XDR has been effective in enhancing the security staff productivity through the strategic delivery of detection and response capabilities. It provides in the time access to information required for proactive response against potential attacks. Not to miss, the subscription model makes it accessible at lower costs.
Cyber-security-as-a-service
The shift to cloud is nowhere near to stop. More than just taking precautions against COVID or any alike situation, cloud saves a lot of money. Enterprises those who have to adopt cost cutting can still avoid the pain of letting employees go by cutting down on infrastructure maintenance. Amidst all this, organizations must not lose the focus from implementing critical security measures, especially when most of them are easily accessible at a lower cost.


Abstract It is safe to believe that the pandemic was a blessing in disguise for the cloud adoption markets. Businesses had no choice but deploy remote working and monitoring infrastructure as far as possible so that the dependency on manual processes is minimal. To give a quick run-through, the cloud spending grew by 37% in


Executive Summary Amidst the propelling adoption of cloud across the enterprise facet Microsoft’s Azure is at the crest of a wave. It is simple, logical and easy to deploy throughout the organization landscape. In all honesty, Azure was already listed among the top 3 cloud platforms in the world before the pandemic happened. By


The internet isn’t what it used to be before the COVID 19 pandemic. Working from home is the new normal and so digital streamed content has gained a lot of significance since the last year. Digital learning and remote working have evolved massively to suit the convenience of people worldwide.


Google Core Web Vitals have been a hot topic in the SEO community ever since they were introduced by Google on May 28, 2020. As per the Google page experience update, these core web vitals now affect rankings on SERPs. And because Google has aimed to provide fast and accessible information to its users, they announced that Google Core Web Vitals will be considered as a ranking factor alongside other UXrelated signals starting May 2021.